|
|
|
Introduction
|
 |
|
You should read the system overview before this.
We now discuss what kind of attacks (by ascending power) can be mounted
against the watermarking system.
Ok. First, there is the original song A. Then, it is marked to produce the
song B.
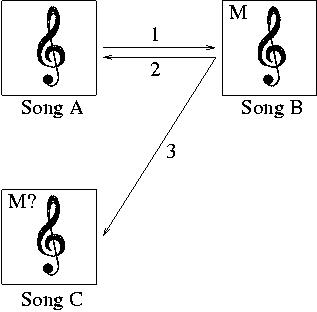
 Then, there are two ways to attack it. The first obvious one, is to recover
the original song A. The other, much easier, is to create a new song C,
which will (a) be audibly close to the original (b) won't have a detectable
mark. Note that there is an attack of that type which works all the time:
ask musicians to decode and re-record the song :)
Then, there are two ways to attack it. The first obvious one, is to recover
the original song A. The other, much easier, is to create a new song C,
which will (a) be audibly close to the original (b) won't have a detectable
mark. Note that there is an attack of that type which works all the time:
ask musicians to decode and re-record the song :)
 So, depending on the understanding of the algorithm you have, we
distinguish three types of attack:
So, depending on the understanding of the algorithm you have, we
distinguish three types of attack:
- Random attack Here, you don't even try to understand
how the marking algorithm works. You just apply some kind of transformation
to the song, and hope the mark can't be detected any more. If you can get
fast answers from an oracle (which was not the case in the contest), this
attack might be feasible. However, you might need a lot of trials before you
actually succeed, and you have to check the quality once you have succeeded.
Furthermore, this attack can hardly be automated.
- Directed attack To mount this attack, you need partial
understanding of the scheme. Then, you will apply transformation suited
to disturb the detection process. For example, in you have understood that
the marking process is only modifying the phase of the signal, you can try
to apply all-pass filters or similar transformations. Naturally, the more
you understand, and the highest your chances of success are. It might be
possible to semi-automate this kind of attack. The only problems are
(a) you cannot be sure the attack will work against every song, (b) you
cannot be sure the final audio quality will be good enough for every song.
- Surgical attack Here, you need an almost complete
understanding of the inner workings of the scheme. The transformation you
apply should simply remove the mark that has been inserted and recover
exactly the original song. This kind of attack is, of course, very powerful.
There aren't any audibility problems any more (the quality is actually
better than the marked version), and you know the attack always succeed.
With such an attack, you could code a filter that would automatically
remove the mark of any song you download to your computer, thus defeating
the whole purpose of the scheme.
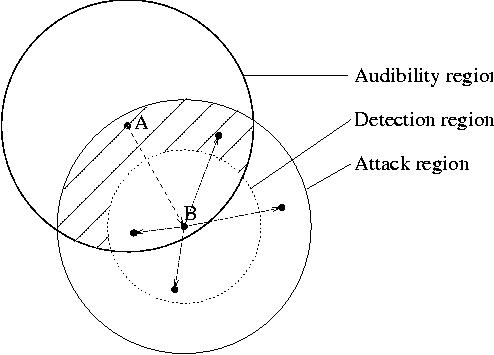
We can more or less summarize these attacks in the following picture.
The original song is A. The marked version B. The zone with the stripes
is where you want to go to defeat the scheme, that is outside the detection
region but in the audibility region (this zone is probably actually
much smaller than on the picture). If you use a random attack, you might
need a lot of time (maybe days) to finally fall in the right zone.
If you use a directed attack, your odds are much better, they might
even be close to 1 if your attack is very directed. Finally, if your
attack is surgical, you win every time :)
|
|
|

