 |
Let us now detail how the entrance to the secure world is checked.
As one may easily figure, two algorithms are going to be involved both in the creation and the detection processes.
The watermarking technology is simply here to enable the gatekeeper distinguish legacy content and new content. If a mark can be found, the content is deemed new.
The identification technology is here to prevent modifications of the LP, notably compression.
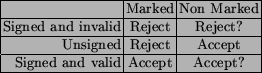
When an LP is trying to enter the secure world, the following checks are made:
 |
The results of the first column are very clear. If the mark is found, the LP is considered new, therefore it should be correctly signed. If it is not, it should be rejected.
The second column is not as clear. If it is unmarked and unsigned, it is supposed to be a legacy LP so it should be accepted. If it is unmarked BUT signed, it means something strange has happened. We are not sure how the test behaves in these cases and the above table only represent our guess.